-
rich commented on the post, Farewell Stephen, on the site Bristol Wireless 7 years, 8 months ago
Thanks for all your support and encouragement over the years Steve and best of luck with your new venture.
-
Christian Wach commented on the post, Cross-party group of MPs: BT should be forced to sell Openreach, on the site Bristol Wireless 8 years, 3 months ago
Wow, just wow!
-
rich commented on the post, Bristol student co-author on paper at Warsaw cryptography conference, on the site Bristol Wireless 9 years, 1 month ago
Excellent, well done Sophie!
-
rich commented on the post, Introducing the anonabox, on the site Bristol Wireless 9 years, 6 months ago
Things aren’t quite as they seem:
-
rich wrote a new post on the site Bristol Wireless 9 years, 6 months ago
 Asus have kindly lent Bristol Wireless a ChromeBox for evaluation and I’ve had a chance to put it through its paces.
Asus have kindly lent Bristol Wireless a ChromeBox for evaluation and I’ve had a chance to put it through its paces.On opening the box I was surprised by its compact form; it’s about the size of a CD case and […]
-
rich posted an update 9 years, 10 months ago
@adelayde hi mike
-
Christian Wach posted an update in the group
 Greenhaven 9 years, 10 months ago
Greenhaven 9 years, 10 months ago@rich This should ping you
-
rich joined the group
 Greenhaven 9 years, 10 months ago
Greenhaven 9 years, 10 months ago -
rich changed their profile picture 9 years, 10 months ago
-
Christian Wach and
 rich are now friends 9 years, 10 months ago
rich are now friends 9 years, 10 months ago -
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
To enable open source ICT to be used by both businesses and individuals through the provision of installation, support and training services.
Bristol Wireless believes that this should be achieved by (being):
Mutually supportive
Socially inclusive
Community orientated
Encouraging reuse and sustainability
Aware of accessibility
Aware of equal opportunities -
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
Introduction
Bristol Wireless Community Co-operative Limited (hereafter referred to as BW) is bound by the laws and regulations governing use of the Data Communications & Services which serve to enable its Customers to use BW’s network and the Internet without interference or harassment from other users. The Bristol Wireless Internet Acceptable Use Policy (hereafter referred to as the AUP) is designed to help facilitate this.
By using the BW Service(s), as defined below, Customer(s) agree(s) to comply with this Acceptable Use Policy and to remain responsible for its/their users. BW reserves the right to change or modify the terms of the AUP at any time, effective when posted on BW’s website at http://www.bristolwireless.net/acceptable-use-policy/. Customer’s use of the BW Service(s) after changes to the AUP are posted shall constitute acceptance of any changed or additional terms.
This AUP applies to all the BW services (Internet, VoIP, hosting) that are used by the Customer.
1. Illegal use
BW services may not be used for illegal, unlawful or harmful purposes, or any activity that interferes with use of the BW network or systems, or the network of any other provider, or interferes with the lawful use of services by other users of BW services.
Use of the BW services for the purpose of spam/e-mail abuse, or any activity that poses a security risk or a violation of privacy to other users of the BW network and the Internet is not permitted.
This prohibition includes, without limitation, material protected by copyright, trademark or any other intellectual property right used without proper authorisation, and material that is obscene or defamatory, constitutes an illegal threat or violates export control laws.
Transmission, distribution or storage of any material in violation of any applicable law or regulation is prohibited.
Failure to adhere to any of the points set out in the AUP is a violation of the agreement.
2. Excessive use
The BW Network is a resource shared by all its customers, the quality of service of which, must not be impaired by any single customer to the detriment of any other(s).
Users of the Service must not make excessive use of the service to the detriment of other users of the Network.
Users making excessive use of the service will be advised about their usage or offered an upgrade to a higher level of service.
Continued excessive usage of the network will be deemed a violation of the AUP and may result in limitation of the service supplied by BW, or may result in the termination of the agreement with BW for use of its Services.
Examples of excessive use include:
Streaming of High Definition Audio/Video(AV) Media at rates greater than 2Mbps (2,000 Kbps) for extended periods (10’s of minutes) of time.
Unregulated use of BitTorrent or other Peer-To-Peer services for the transfer of files that adversely affects the Quality Of Service (QoS) of the BW network.
Transfer (total of upload and download) of more than 20Gigabytes (20,480 Megabytes) in a single 24 hour period; or
Transfer of more than 500Gb (512,000 Megabytes) per month.3. The network
The user acknowledges that BW is unable to exercise control over the content of the information passing over the Network. Therefore, BW is not responsible for the content of any message whether or not the posting was made by a Customer.
The Network may be used to link to other networks worldwide and the user agrees to conform to the acceptable use policies of these networks.
In addition, the user undertakes to conform to the Internet protocols and standards.
The user may not circumvent user authentication or security of any host, network, or account (commonly referred to as “cracking” or “hacking”), nor interfere with service to any user, host, or network (referred to as “denial of service attacks”), nor intercept or monitor wireless network traffic.
Without prejudice to the above, BW considers that any application that overloads the Network by whatever means will be considered as making profligate use of the Network and is as such NOT allowed. Use of IP multicast other than by means provided and co-ordinated by BW is likewise prohibited.
Users who violate systems or network security may incur criminal or civil liability. BW will co-operate fully with investigations of suspected criminal violations and the violation of systems or network security under the leadership of law enforcement or relevant authorities.
4. System and network security
Violations of system or network security are prohibited and may result in criminal and civil liability. BW will investigate incidents involving such violations and will involve and will co-operate with law enforcement authorities if a criminal violation is suspected.
Examples of system or network security violations include, without limitation, the following:
Unauthorised access to or use of data, systems or networks, including any attempt to probe, scan or test the vulnerability of a system or network or to breach security or authentication measures without the express authorisation of the owner of the system or network;
Unauthorised monitoring of data or traffic on any network or system without express authorisation of the owner of the system or network;
Interference with service to any user, host or network including, without limitation, mail-bombing, flooding, deliberate attempts to overload a system and broadcast attacks;
Forging of any TCP/IP packet header or any part of the header information in an email;
Interception or monitoring wireless network traffic.If approached with complaints relating to any of the above violations, BW will co-operate with and assist the Police and law enforcement bodies with their investigations in order to bring such misuse and violations to an end.
5. Email
It is explicitly prohibited to send unsolicited bulk mail messages (“junk mail” or “spam”) of any kind (commercial advertising, political tracts, announcements, etc.).
It is also explicitly prohibited to allow others to send unsolicited bulk mail messages either directly or by relaying through the User’s systems. For the avoidance of doubt, users must ensure that their systems cannot be used for relaying. Users may not forward or propagate chain letters nor malicious e-mail. Aiding or abetting others to send bulk email is prohibited. This includes providing software, names and addresses of spam firms and selling of bulk email address databases. BW will regularly check customer address space to ensure that there are no open relays within its network.
A user may not solicit mail for any other address other than that of the user, except with full consent of the owner of the referred address.
6. Customer Responsibilities
Customers remain solely and fully responsible for the content of any material posted, hosted, downloaded/uploaded, created, accessed or transmitted using the BW Services. BW has no responsibility for any material created on the BW network or accessible using it’s Services, including content provided on third-party websites linked to the BW network. Such third-party website links are provided as Internet navigation tools for informational purposes only, and do not constitute in any way an endorsement by BW of the content(s) of such sites.
Customers are responsible for taking prompt corrective action(s) to remedy a violation of AUP and to help prevent similar future violations.
Complaints regarding illegal use or system or network security issues, email abuse or spamming should be sent to support@bristolwireless.net
INDIRECT OR ATTEMPTED VIOLATIONS OF THIS POLICY AND ACTUAL OR ATTEMPTED VIOLATIONS BY A THIRD PARTY ON BEHALF OF A BRISTOL WIRELESS COMMUNITY CO-OPERATIVE CUSTOMER OR A CUSTOMER’S END USER SHALL BE CONSIDERED VIOLATIONS OF THIS POLICY BY SUCH CUSTOMER OR END USER.
Version 2.0, September 2012
-
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
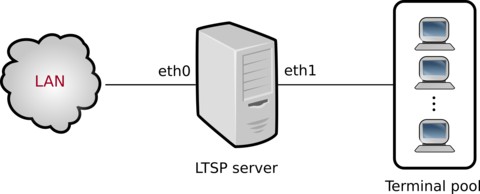
At Bristol Wireless we’ve been using LTSP* (Linux Terminal Server Project) since we were founded in 2002. We’ve always found it to be very reliable both for running our lab in Bristol, as well as providing public access/training suites in both fixed locations and for temporary/mobile ICT for events.
LTSP is a client/server based computer system allowing multiple users simultaneous access to the same machine. Linux is a free operating system that also come complete with a free office suite, web browsers and media players, etc., and can run applications from Linux and Windows servers. The system runs on a single server, such that routine maintenance, backups and updates of the LTSP server can be carried out remotely. LTSP thin clients contain no moving parts, hard drives, optical drives, etc. and have only minimal memory, meaning that thin clients are quieter than conventional desktop PCs and consume considerably less power, further reducing costs, an important factor to consider when looking at ‘greening’ ICT to make it more environmentally friendly. LTSP is a flexible, efficient platform that’s enabling schools, businesses and organisations of all kinds all over the world to install and deploy open source desktop workstations easily.
Thin clients (also known as terminals) can be bespoke shiny new units or refurbished legacy PCs and may be used for conventional tasks: to browse the web, send email, create documents, graphics and run other desktop applications.
LTSP not only improves Total Cost of Ownership (TCO), but more importantly provides increased value over traditional computing solutions.
A public access LTSP thin client in a secure cabinet at Easton Community Centre Linux thin clients have proved to be extremely reliable because they’re tamper-proof (ideal for public access suites) and Linux is a very secure, stable operating system.
Easton Community Centre’s LTSP public access suite – a case study
Various real world scenarios exist where LTSP has been running continuously for a number of years without serious problems. One example is Easton Community Centre. The original project entailed the installation of seven LTSP workstations for public use in the foyer of Easton Community Centre in Kilburn Street, Easton, Bristol. In keeping with our green credentials, this project used donated Compaq workstations originally used as desktops by the National Health Service for the thin clients. A Dell server was chosen to run the suite and all the user applications. It proved to be both very low-powered and very efficient.
[caption id="attachment_3809" align="aligncenter" width="400"]
 A public access LTSP thin client in a secure cabinet at Easton Community Centre[/caption]
A public access LTSP thin client in a secure cabinet at Easton Community Centre[/caption]This installation has since been updated courtesy of grant funding with bespoke thin clients being housed in robust, tamper-proof custom cases designed by Bristol Wireless. These systems have proved to be very reliable: they run in what’s known as kiosk mode; this means that when the user closes the web browser all history is lost and any user data stored in the home directories is also cleared when the terminals are turned off.
LTSP is distributed under Version 2 of the GNU General Public License (GPL), meaning it’s free of licensing fees and always will be.
Please contact us for more information on LTSP or to arrange a demonstration. Alternatively, download our non-technical LTSP leaflet.
* LTSP is a registered trademark of DisklessWorkstations.com, LLC
-
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
The best ways to get involved in the project are to sign up to our mailing list and start posting or to come to a meeting; these are usually held on the second Monday of each month, but contact us for details if […]
-
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
Bristol Wireless specialise in the deployment of open source and Linux on the desktop and server.
Migration is the act of moving from one operating system to another (e.g. Microsoft Windows to Linux). If you’re considering migrating your IT, Bristol Wireless can help.
Consultancy
Site surveys
Evaluations
Comprehensive reporting and analysis
Advice on which sorts of migration are both practical and cost-effective
Tailored, affordable support packages and training
Fully managed IT systems tailored to your organisation
No vendor lock-in
Remote administration, reducing support costs, response time and mileage
Consultation with experienced techniciansTraining
We have many years experience of providing in-house training in open source and Linux.
Support
We have trained support staff available during business hours from Monday to Friday (public holidays excepted).
We have staff available within the Bristol area to offer on-site support or we can partner with other open source consultants elsewhere in the country to ensure your systems are fully supported.
Please see our dedicated support page.
Technical detail
Bristol Wireless will help you to migrate from your present operating system(s) to Linux.
Low energy, low cost, low maintenance and reliable IT systems
Tailor-made software built on Linux
Wireless and wired networking
Inexpensive VoIP (web-based) telephone systems
Server and desktop systems
Database design/migration
ADSL connectivity
Managed servers and virtual servers
Encrypted off-site backup and disaster recovery
Web and mail hosting consultancy
A range of LTSP (thin client) optionsWhy we recommend Linux and other Free and Open Source Software (FOSS)
FOSS is easily adaptable and can be modified to suit your needs. In other words, tailor your software to your business, not your business to your software
FOSS applications are freely available to copy, adapt and share with no licensing costs or restrictions on volume usage.
FOSS is scalable and FOSS operating systems and software run on PCs, Macs, supercomputers, PDA’s and mobile phones, multimedia devices, etc.
Improved security; fewer vulnerabilities and bug are fixed speedily; fewer viruses, Trojans, worms; no spyware or malware.
Integrated accessibility software.
Linux can reduce power requirements and result in significant energy savings. Open source systems have lower system requirements than some other operating systems and will happily run on older hardware, extending its service life. -
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
When ethical business people want to sell something they publicise, improve their product and make sure theirs is the best. They defend their intellectual property to make sure it is distributed in ethical way – whether is a closed source or open source product.
When unethical people whose product might not be as good as the competition want to control a market so that no one else can get their foot in the door, they will try all sorts of tricks.
One of those tricks is FUD, standing for Fear, Uncertainty and Doubt. The idea is to try and introduce one, two, or all of the above into people’s perceptions of the competing product. The assertions might not be true, have any fact to back them up, and – more dangerously – might be implicit rather than explicit, so that it is unconsciously absorbed.
This page is to help us see that FUD by documenting it, but first, a word of warning…
Open Source zealots beware! It’s not just Microsoft that cast FUD, the open source posse does too…
If there were a competitive advantage to this software we’d be using it, wouldn’t we?
This is a fantastic baseless fact that you can be thrown around when cornered. It has an undercurrent of “I am a professional therefore anyone else’s thinking on this issue is wrong, even if they have more successful business models and a better car”. People will still fall for it though.
The software is only secure because no-one uses it, so it’s not a target
Perhaps they just have better security model? Wake up and smell the coffee.
Our product doesn’t sell more because of uncompetitive practices, it’s because it is so much better
And people watch Eastenders because it is the best TV drama. Kylie Minogue is one of the worlds best musicians. Come on, saying it’s better because it sells more is just disingenuous, especially from those running cartels.
There is no FUD; people are scared for a reason
When people are scared about something they haven’t tried out, it must be because of something they’ve heard about; that something is FUD. We’re are going round in circles. There is no Kieser Sosey. There are however documents known as the Halloween documents.
Our friends at insert_company name_ could did not find any increase productivity with this product
I know someone who can’t use a toaster. So?
Stop it!
Things to remember (that can also be used for uncertainty and doubt):
Fear is a powerful way of manipulating people
Fear is a useful response which helps us guide our future
If you use fear to manipulate make sure it has a base
If you spot someone using fear without any factual base, point it out to them
Never trust people who use baseless fear tactics, and don’t see it as an error – these people are known as socio-paths and should not be trusted -
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
It is quite possible to hold constructive meetings via IRC. Indeed, organisations as large as the Wikimedia Foundation still use IRC for arranging major events, such as Wikimania. Follow the simple rules below to avoid disappointment.
[caption id="attachment_5389" align="aligncenter" width="600" caption="The Xchat IRC client. Picture courtesy of Wikimedia Commons"]
 [/caption]
[/caption]Having an effective meeting online
It is much harder to hold a meeting online than one in person because you can’t easily indicate to the person running the meeting when you want to speak. There are a few basic guidelines to make our meetings go smoothly.The moderator is the person leading the chat. S/he will normally be marked by an @ symbol next to their name. The moderator will give people permission to speak and generally try to keep order in the meeting.
Format
If you want to indicate that you agree with the current speaker, or have a question, you can ‘virtually’ put your hand up:! = I have something to say
? = I have a question to ask
… = I’m still speaking; please wait for me to finish
* = I agree with what you’ve just saidIf you’ve been speaking for a while, finish your speech by saying “end”.
Although they don’t seem like much, just these simple codes mean that people don’t need to interrupt each other, and the moderator can easily tell what’s going on and keep things working.
Guidelines courtesy of the Woodcraft Folk.
-
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
Yes indeed. On 1st April 2007, we published the manpage content for the Wireless Cider Transmission Protocol (wctp) reproduced below.
Introduction
This is the manual for wctp – wireless cider transmission protocol. A proper Unix/Linux manpage is being prepared.Name
wctp – Wireless Cider Transmission ProtocolSynopsis
wctp ~[-acefghlqy] siteDescription
wctp allows the user to transfer cider, perry or other apple and pear-based alcoholic beverages between network sites. Using TCP/IP (transmission control protocol for imbibing pints), wctp encodes cider from a local file system into packets suitable for FTP (fermentation transfer protocol) delivery at a remote IP site.Example:
wctp -c”THATCHERS”-2g -l 194.201.189.210
The above example is an instruction to sent 2 gallons of Thatchers with lemons (for adding a slice to one’s drink) to IP address 194.201.189.210. This is the IP address of 10 Downing Street, official residence of the British Prime Minister, where booze is urgently needed to complement the incompetence.
Notes
Both the source and destination sites must be running wctp-daemon. In addition, geographical location may hamper free use of this protocol. In certain parts of the United States of America, local restrictions exist on the shipping of alcohol across state lines. In the European Union, under internal market regulations unlimited quantities of cider may be transferred between Member States provided duty has been paid. It is not advisable to attempt use of this protocol in strict Islamic countries where the consumption of alcohol is banned.See also
uubpAuthor
Steve Woods,woodsy (at) bristolwireless.net, with acknowledgements to the original authors of uubp -
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
The sky appears blue (instead of black) because light passing through the air hits tiny particles like dust and pollen. These tiny particles are large enough to reflect blue light, but red light (which has a longer wavelength) is not reflected nearly as much. So the result is that the blue light gets scattered by the particles, and you see it when you look up.
The other side of this is sunset, when the sun appears reddish-orange low on the horizon. That’s because the light rays have to pass through a lot of air (and particles) before they get to your eyes, and all the blue light was scattered away and dispersed. That leaves only the red end of the spectrum to penetrate the atmosphere and reach your eyes.
At noon, the sun is coming straight down and only passing through ten miles of atmosphere or so. At sunset, the same light has to pass through many hundreds of miles of air to reach you. You will see more dramatic sunsets (redder and darker) when there’s a lot of dust, smoke or pollen in the air. When volcanic eruptions occur, intense sunset colours are seen around the world, sometimes for a couple of years after the event (as happened after Krakatoa. Ed.).
If the air is truly pure, it doesn’t scatter light much at all. If you climb up above the atmosphere or nearly to the top of it in an aeroplane, the sky appears black, not blue. If we had particle-free air, the sky would likewise appear black instead of blue. But we don’t.
-
Christian Wach wrote a new post on the site Knowledge Base 10 years ago
Introduction
We are committed to safeguarding the privacy of our website’s visitors; this policy sets out how we will treat your personal information.
What information do we collect?
We may collect, store and […] - Load More

Hi rich, this is cool isn’t Christian clever 🙂
Hello
Oooh a kitten!